Keep your business safe from cyber risks and compliant with current standards (ISO/IEC 27001)

DEFENCE is the platform that allows you to fully manage cyber & IT security ensuring compliance with the highest standards in use
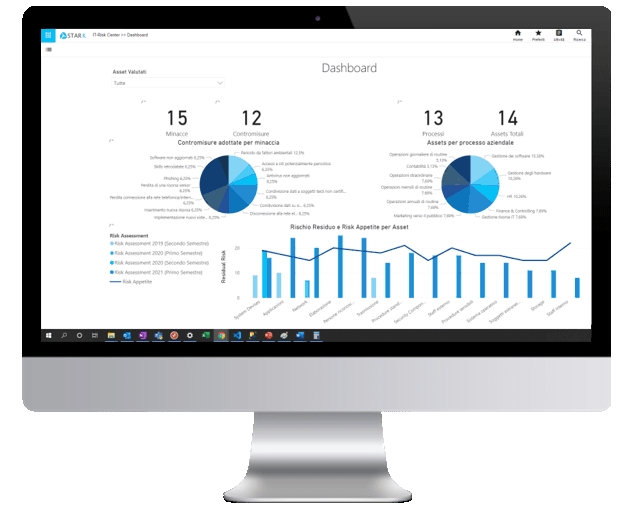
Why choose DEFENCE
- Identification, evaluation, monitoring and control of the organization's IT risks, in a complete and integrated way.
- Management of IT incidents in an organized way by shortening resolution times and by limiting legal responsibilities (d.lgs 231).
- Management of IT suppliers and related document flows by optimizing their timing and governing the formal storing process.
- Risk Assessment on each identified asset and to identification of vulnerabilities that put IT security at risk.
- Reports and dashboards useful for capturing situations and obtaining information.
- Based on concrete, operational and updated management methodology.
- Modular, flexible and customizable platform.
PLUS
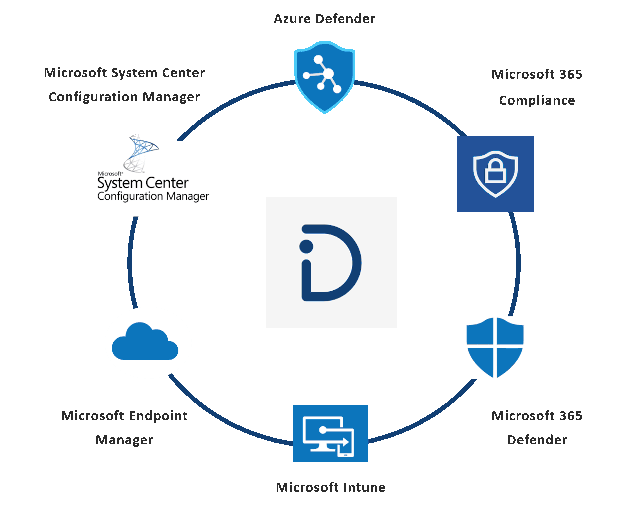
Automated input data
Input data of the DEFENCE modules can be generated automatically using specific software from the Microsoft suite.
Specialized consultancy
Our partners offer a specialized consultancy in order to support the customer in all phases of analysis and implementation of the system.
Integrated Modules
Assets Inventory
The simple, immediate and real-time updated IT asset management solution
IT Risk Control Model
Mapping business processes and IT assets with full knowledge of the associated risks.
Risk Assessment
The solution to digitise the IT risk assessment process in line with the latest mandatory regulations.
Mapping Deficiency Management
Map IT deficiencies, associate an ad hoc treatment plan and carry out a new Risk Assessment verification.
Suppliers Management
Manage the identification and assessment of risks and deficiencies in the IT supply chain.
IT & Data Protection
Set up corporate IT governance with 360° management of IT treatments in an integrated repository.
Features
- Assets Inventory
- IT Risk Control Model
- Risk Assessment
- Mapping and Deficiency Management
- Suppliers Management
- IT & Data Protection
Assets Inventory
Asset inventory is the solution for IT assets management within the organization.
The classification of IT assets generates a single updated and categorized inventory to act on for management control.
Asset inventory keeps track of all IT resources, providing a sort of ID of the asset.
- With DEFENCE asset inventory is easy, immediate and updated in real time.
- Gives an updated view of all company assets.
- Allows the detection of all IT assets and allows to manage their life cycle in order to carry out updates or disposals.
IT Risk Control Model
Allows business processes and IT asset mapping, cataloging sub and counter measures.
IT asset are related to business processes, associated with possible threats and relative countermeasures.
The aim is to ensure maximum knowledge of the risk associated with each identified asset
- Process management and organization
- Association of in use assets
- Assessment of related threats
- Countermeasures
Risk Assessment
The solution leverages collaboration and approval processes by involving and interacting with the different user owners of the impacted processes.
- Digitizes the Risk Assessment process, monitoring the progress and the results obtained with constant updating.
- Performed on assets is based on a methodology that leverages impact quantification against three GDPR scenarios: confidentiality, integrity, and data availability.
- Exploits the risk appetite threshold to highlight the gaps and activate countermeasures.
- Calculates and monitors residual risk and its acceptance
Mapping and Deficiency Management
DEFENCE allows to manage the complete mapping process and shortcomings up until their resolution.
- Allows the monitoring of all issues and for each identified shortcoming it associates a treatment plan.
- Monitors all issues related to IT assets
- Sets up, schedules and manages treatment plan
- Organizes shortcomings into categories and coordinates the operational "next step"
Suppliers Management
Thanks to DEFENCE it is possible to associate a specific treatment plan for each shortcoming and carry out a new Risk Assessment to determine if the shortcoming has been solved
- Monitors all issues related to IT assets
- Sets up, schedules and manages treatment plan
- Organizes shortcomings into categories and coordinates the operational "next step"
IT & Data Protection
DEFENCE's module for setting up and demonstrating corporate IT governance with 360° management of IT treatments and a single integrated repository.
- Organizes Data Protection management by formalizing Reports and control dashboards.
- You will have a single integrated repository for the entire company to store and manage all aspects related to nominees, records, DPIAs...
Funzionalità
Assets Inventory
Asset inventory is the solution for IT assets management within the organization.
The classification of IT assets generates a single updated and categorized inventory to act on for management control.
Asset inventory keeps track of all IT resources, providing a sort of ID of the asset.
- With DEFENCE asset inventory is easy, immediate and updated in real time.
- Gives an updated view of all company assets.
- Allows the detection of all IT assets and allows to manage their life cycle in order to carry out updates or disposals.